Big Idea 5.5 and 5.6
Big Idea 5.5 and 5.6
5.5 Legal and Ethical Concerns
When you create a GitHub repository it requests a license type. Review the license types in relationship to this Tech Talk and make some notes in your personal blog.
- MIT License
- The software may be used, copied, modified, and distributed with permission.
- The software has few limitations and can be used for both business and non-commercial enterprises.
- Ensures that the original copyright and license information are included and permits anybody to use, alter, and distribute the licensed software for any reason, including commercial use.
- GPL License
- Software users are free to use, alter, and distribute the software for any reason.
- They can also choose to charge a fee or give it out for free.
- Anyone who obtains a copy of the software must have access to the source code.
In your blog, summarize the discussions and personal analysis on Software Licenses/Options, Digital Rights, and other Legal and Ethical thoughts from this College Board topic.
- The conditions under which software can be used, updated, and distributed are outlined in its license.
- When thinking about ethical issues, digital rights like privacy and intellectual property rights are crucial. For instance, licensing can stop music from being copied illegally so that creators can claim credit for their work.
- For software developers, this is crucial since it enables creators to maintain control over their work and defend their legal rights against data theft.
- Digital rights, software licenses, and legal and ethical issues are all intricately intertwined and have an impact on how software is developed, distributed, and used.
Make a license for your personal
- The use of the program is more flexible under an MIT License. The GPL license mandates that derivative works be granted the same license as the software’s original version. For more freedom, we choose the MIT license. Code can be more easily distributed, which may be advantageous to other users.
- This is our project License File
- This is my personal License File
Extra - Research
The objectives and principles of the open-source project and the community’s choices determine how popular certain licenses are. To encourage collaboration and the sharing of innovations, for instance, some projects can opt for the GPL, while others would opt for the Apache License 2.0, which permits commercial use and offers patent protection. Before selecting a license, it is crucial to understand its ramifications and how it will affect the demands and objectives of the open-source project in general.
From the Statista here is the percentage of most popular opensource license
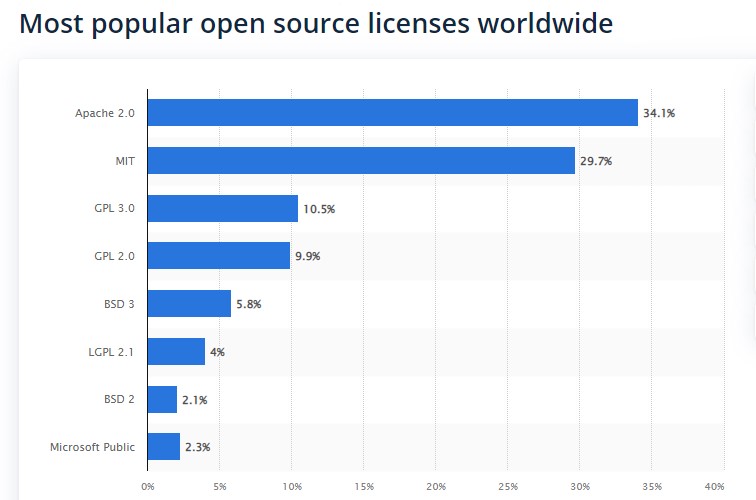
There are several popular open-source licenses, but the three most widely used licenses are:
MIT License: The MIT License is a permissive license that allows for the use of open-source software in commercial and non-commercial applications. It has minimal restrictions and is considered a simple license to understand and apply.
GPL (GNU General Public License): The GPL is a copyleft license that requires derivative works to also be released under the same license. This ensures that any modifications to the software must be open-sourced, promoting collaboration and sharing of improvements.
Apache License 2.0: The Apache License 2.0 is a permissive license that is similar to the MIT License but has a few additional provisions, such as a requirement to provide attribution and a patent grant.
5.6 Safe Computing
Describe PII you have seen on project in CompSci Principles.
- On the login page, you can see projects in CSP that include PII. People’s name and email are included in their login information when they access a website on our website.
What are your feelings about PII and your personal exposure?
- Since you may be followed online using PIIs, I believe they could be hazardous because I don’t want to be followed. It is crucial to make sure that the information you are providing is to a secure website where your information won’t be stolen because PIIs are required for login and the user experience.
Describe good and bad passwords? What is another step that is used to assist in authentication.
- A strong password is one that is difficult for others to decipher and contains no personal information.
- A bad password is abcdef or password123 or something that can be easily guessed.
Try to describe Symmetric and Asymmetric encryption.
- Symmetric encryption, Using the same key for both encryption and decryption, symmetric encryption is a quick and effective method of encryption
- Asymmetric encryption, is when the encryption and decryption processes employ two separate keys. The private key, which is needed to decrypt the data and must be kept secret, is used to encrypt the data and is widely distributed.
Provide an example of encryption we used in AWS deployment.
AES-512 encryption
Describe a phishing scheme you have learned about the hard way. Describe some other phishing techniques.
- People using phony lotteries to steal personal information is an example of phishing I’ve witnessed. People will text you requesting your address and other personal information after telling you that you have won money. It’s not good.
- Malicious websites, voicemails, and emails are examples of further phishing.
Extra - Research
NIST Guidelines for Password Protection.
- NIST recommends a password policy that requires all user-created passwords to be at least 8 characters in length
- All machine-generated passwords to be at least 6 characters in length.
- Additionally, NIST recommended to allow passwords to be at least 64 characters as a maximum length.
Here are the ways to keep our Passwords Strong and Secure
- Use a password manager to keep track of your passwords
- Write your login credentials down and save it safely(yes!!)
- Find out if your passwords have been stolen. Mozilla’s Firefox Monitor and Google’s Password Checkup can show you which of your email addresses and passwords have been compromised in a data breach so you can take action
- Avoid common words and character combinations in your password
- Longer passwords are better: 8 characters is a starting point
- Don’t recycle your passwords
- Avoid using passwords known to be stolen
- No need to periodically reset your password
- Use two-factor authentication.
Commonly used & breached passwords
- Passwords that are known to be commonly used or compromised should not be used again.
- For example, we should disallow passwords in lists from breaches.
- The Have I Been Pwned? database, contains 570+ million passwords from breaches, previously used passwords, well-known commonly used passwords, and context-specific passwords.
- Here is the link to Have I Been Pwned?